In this article I'll get the customer sites connected up in a very simple VRF.
The first step is to create a VRF for the customer sites to use. This is done by naming it on each PE router, assigning a route distinguisher (RD) and setting route targets (RT) for BGP to use. The simplest way to do this is to allocate the RD in the format AS:nn where AS is the customers autonomous system number, then to assign the same value to the RT.
In this case the customers AS will be 1 so the configuration is:
ip vrf VPN_ONE
rd 1:1
route-target export 1:1
route-target import 1:1
This creates the VRF on the two PE routers, to make use of them the interfaces leading to the CE routers have to be put into the VRF:
PE1#show run int fastEthernet 0/0
Building configuration...
Current configuration : 153 bytes
!
interface FastEthernet0/0
description To CE1
ip vrf forwarding VPN_ONE
ip address 10.0.255.2 255.255.255.252
end
PE2#show run int fastEthernet 0/0
Building configuration...
Current configuration : 153 bytes
!
interface FastEthernet0/0
description To CE2
ip vrf forwarding VPN_ONE
ip address 10.0.255.5 255.255.255.252
end
At this stage the CE routers can contact their directly connected PE router, but they cannot contact each other. They are also completely segregated from the backbone of the service providers network. They are given a default route via the PE router:
CE1#show ip route
[snip]
S* 0.0.0.0/0 [1/0] via 10.0.255.2
CE1 to PE1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.255.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/5/8 ms
CE1 to CE2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.255.6, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
CE1#ping 10.0.0.9
CE1 to P1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.9, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
To allow communication between the two customer sites (the two CE routers), we need to have MP-BGP advertising the vpnv4 routes between the two PE routers. Because there aren't really any customer sites yet, just the links that are directly connected between CE and PE, we can "redistribute connected" routes on the PE routers so that MP-BGP advertises them with the RD for this customers VRF.
This is done as follows:
PE1#config term
Enter configuration commands, one per line. End with CNTL/Z.
PE1(config)#router bgp 65001
PE1(config-router)#address-family ipv4 vrf VPN_ONE
PE1(config-router-af)#redistribute connected
With the same on PE2. Now we can look at the BGP routes specific to this VPN and see the connected interfaces are being advertised:
PE1#show ip bgp vpnv4 vrf VPN_ONE
BGP table version is 17, local router ID is 10.255.255.51
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 1:1 (default for vrf VPN_ONE)
*> 10.0.255.0/30 0.0.0.0 0 32768 ?
*>i10.0.255.4/30 10.255.255.52 0 100 0 ?
As the VRF instances on the two PE routers can now see each other, they are able to forward traffic between the two CE routers. The customer sites are now linked up:
CE1#ping 10.0.255.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.255.6, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/11/16 ms
So a very basic network setup, two sites able to communicate over a WAN. The PE router configuration is given below, snipped for brevity. Points to note are:
- VRF VPN_ONE defined.
- OSPF running internal to the Service Provider WAN, not visible to CE1 attached to f0/0.
- BGP running between PE1 and PE2, advertising vpnv4 routes to allow the VRF communications.
hostname PE1
!
ip vrf VPN_ONE
rd 1:1
route-target export 1:1
route-target import 1:1
!
interface Loopback0
ip address 10.255.255.51 255.255.255.255
!
interface FastEthernet0/0
description To CE1
ip vrf forwarding VPN_ONE
ip address 10.0.255.2 255.255.255.252
!
interface Serial0/0
description To P1
ip address 10.0.0.1 255.255.255.252
mpls ip
!
interface Serial0/1
description To P2
ip address 10.0.0.5 255.255.255.252
mpls ip
!
router ospf 1
router-id 10.255.255.51
network 10.0.0.0 0.255.255.255 area 0
!
router bgp 65001
bgp router-id 10.255.255.51
neighbor 10.255.255.52 remote-as 65001
neighbor 10.255.255.52 update-source Loopback0
!
address-family ipv4
neighbor 10.255.255.52 activate
exit-address-family
!
address-family vpnv4
neighbor 10.255.255.52 activate
neighbor 10.255.255.52 send-community extended
exit-address-family
!
address-family ipv4 vrf VPN_ONE
redistribute connected
exit-address-family
To try and show a bit more of the segregation that is now in place, look at the routing table on PE1. Note that it does not contain any information from the VRF VPN_ONE on router PE2 (such as the CE2 IP address of 10.0.255.6), also note that PE2 is not able to directly contact CE2, although it can contact it via the VRF "VPN_ONE":
PE1show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 8 subnets, 2 masks
O 10.0.0.8/30 [110/128] via 10.0.0.2, 00:26:46, Serial0/0
O 10.0.0.12/30 [110/128] via 10.0.0.6, 00:26:46, Serial0/1
C 10.0.0.0/30 is directly connected, Serial0/0
C 10.0.0.4/30 is directly connected, Serial0/1
C 10.255.255.51/32 is directly connected, Loopback0
O 10.255.255.52/32 [110/129] via 10.0.0.6, 00:26:46, Serial0/1
[110/129] via 10.0.0.2, 00:26:46, Serial0/0
O 10.255.255.102/32 [110/65] via 10.0.0.6, 00:26:46, Serial0/1
O 10.255.255.101/32 [110/65] via 10.0.0.2, 00:26:46, Serial0/0
PE1ping 10.0.255.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.255.6, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
PE1#ping vrf VPN_ONE ip 10.0.255.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.255.6, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/6/8 ms
The following diagram should help make several things clear:
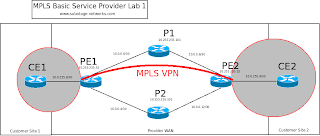
The first thing is that I'm a network engineer and not an artist for good reason!
The second is that we've now managed to overlay a customer network onto the service provider network, the two customer sites are segregated IP networks from the SP backbone. The network VPN_ONE is shown by the grey shaded areas and bounded by red.


