To show some of the finer points of Checkpoint VPNs I'll rig up a test lab with a site-to-site VPN linking a Cisco IOS router and a Checkpoint R65 splat box.
This article is not intended to be a general VPN introduction, rather the specifics of Checkpoint/Cisco interaction.
The network will look like this:
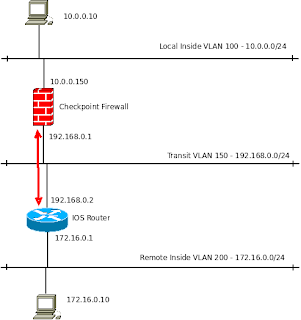
The local end is using 10.0.0.0/24, the Smart Center sits in this subnet.
The VPN traffic is shown by the red arrow. I'm using a transit network, VLAN 150 - 192.168.0.0/24 but this will probably be the internet in most cases.
The first VPN is going to be very simple, no NAT involved anywhere.
Cisco IOS Setup
In this case we need a static route configured on the IOS router to ensure traffic for the remote LAN goes out of the correct interface:
ip route 10.0.0.0 255.255.255.0 192.168.0.2In reality you may not need this as for internet-based site-to-site VPNs the routers default route often does the job.
Now the five steps to create a VPN, handy bit of ISCW revision!
- Define the ISAKMP (phase 1) policy.
- Define the IPsec (phase 2) policy.
- Create the crypto ACL specifying interesting traffic.
- Make the crypto map to bind it all together.
- Apply the crypto map to an interface.
1 - ISAKMP policy
crypto isakmp policy 10
encr aes 256
hash sha
authentication pre-share
group 2
crypto isakmp key cisco address 192.168.0.1
2 - IPsec policy
crypto ipsec transform-set TESTSET esp-aes 256 esp-sha-hmac
3 - Crypto ACL
Define here what traffic should be encrypted.
ip access-list extended VPN_INTERESTING_TRAFFIC
permit ip 172.16.0.0 0.0.0.255 10.0.0.0 0.0.0.255 log
4 - Crypto Map.
crypto map VPN_MAP 10 ipsec-isakmp
set peer 192.168.0.1
set transform-set TESTSET
set pfs group2
match address VPN_INTERESTING_TRAFFIC
5 - Apply to an interface
Cisco_Router(config)#interface fastethernet 0/0
Cisco_Router(config-if)#crypto map VPN_MAP
*Mar 1 00:25:33.187: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
If you see the "ISAKMP is ON" message then it's looking good. If you get errors then check whether your hardware and software is supported, as an example some of the 8xx series routers cannot do AES encryption and I don't think IPsec is supported on any of the standard IOS images.
Part 2 goes over configuration of the Checkpoint end.
Read more...



