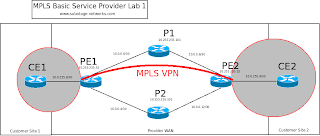
The network topology is as before.
EIGRP is fairly easy to configure in this case. The CE router is just configured as per a vanilla EIGRP network with no special entries needed, on router CE1:
CE1#show ip int brief | inc up
FastEthernet0/0 10.0.255.1 YES NVRAM up up
FastEthernet0/1 172.16.1.1 YES NVRAM up up
CE1#show run | section eigrp
router eigrp 1
network 10.0.0.0
network 172.16.0.0
no auto-summary
FastEthernet0/0 10.0.255.1 YES NVRAM up up
FastEthernet0/1 172.16.1.1 YES NVRAM up up
CE1#show run | section eigrp
router eigrp 1
network 10.0.0.0
network 172.16.0.0
no auto-summary
On the PE router it is fairly straightforward, EIGRP is configured with an "address-family ipv4 vrf VRFNAME" command. The bit to note is the "autonomous-system X" line which tells the router what EIGRP AS is running in the VRF.
PE1#show run | section eigrp
router eigrp 1
auto-summary
!
address-family ipv4 vrf VPN_ONE
redistribute bgp 65001 metric 10000 20 255 1 1500
network 10.0.255.0 0.0.0.3
no auto-summary
autonomous-system 1
router eigrp 1
auto-summary
!
address-family ipv4 vrf VPN_ONE
redistribute bgp 65001 metric 10000 20 255 1 1500
network 10.0.255.0 0.0.0.3
no auto-summary
autonomous-system 1
Any show commands on the PE router must include the VRF statement, e.g.:
PE1#show ip eigrp vrf VPN_ONE neighbors
IP-EIGRP neighbors for process 1
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 10.0.255.1 Fa0/0 11 00:06:48 6 200 0 5
IP-EIGRP neighbors for process 1
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 10.0.255.1 Fa0/0 11 00:06:48 6 200 0 5
As with OSPF (solved by sham links), there is potential for problems with EIGRP if you have backdoor links between sites. The administrative distance of EIGRP internal routes is 90 whereas the iBGP routes AD is 200. To avoid this the pre-bestpath cost BGP extended community value is used.
The Cisco article on the cost community is here. Basically it allows the BGP routing decision process to be overridden by the cost community value which is split into two parts, the first being called the POI (Point-of-Insertion) which is the position in the routing process (e.g. before the normal BGP decision hooks such as weight, local pref, route origin) and the second part being a value that is copied from the EIGRP composite metric. This allows routes to be chosen based purely on the EIGRP metric and BGP factors are ignored.
Unlike sham links this is automatically enabled, here is the route to 172.16.2.0 as seen by BGP:
PE1#show ip bgp vpnv4 vrf VPN_ONE 172.16.2.0
BGP routing table entry for 1:1:172.16.2.0/24, version 11
Paths: (1 available, best #1, table VPN_ONE)
Not advertised to any peer
Local
10.255.255.52 (metric 129) from 10.255.255.52 (10.255.255.52)
Origin incomplete, metric 100, localpref 100, valid, internal, best
Extended Community: RT:1:1 Cost:pre-bestpath:128:307200 0x8800:32768:0
0x8801:1:51200 0x8802:65281:256000 0x8803:65281:1500
mpls labels in/out nolabel/23
BGP routing table entry for 1:1:172.16.2.0/24, version 11
Paths: (1 available, best #1, table VPN_ONE)
Not advertised to any peer
Local
10.255.255.52 (metric 129) from 10.255.255.52 (10.255.255.52)
Origin incomplete, metric 100, localpref 100, valid, internal, best
Extended Community: RT:1:1 Cost:pre-bestpath:128:307200 0x8800:32768:0
0x8801:1:51200 0x8802:65281:256000 0x8803:65281:1500
mpls labels in/out nolabel/23
The route is then received on CE1 with an advertised metric of 307200:
CE1#show ip eigrp top 172.16.2.0 255.255.255.0
IP-EIGRP (AS 1): Topology entry for 172.16.2.0/24
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 332800
Routing Descriptor Blocks:
10.0.255.2 (FastEthernet0/0), from 10.0.255.2, Send flag is 0x0
Composite metric is (332800/307200), Route is Internal
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 3000 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 2
IP-EIGRP (AS 1): Topology entry for 172.16.2.0/24
State is Passive, Query origin flag is 1, 1 Successor(s), FD is 332800
Routing Descriptor Blocks:
10.0.255.2 (FastEthernet0/0), from 10.0.255.2, Send flag is 0x0
Composite metric is (332800/307200), Route is Internal
Vector metric:
Minimum bandwidth is 10000 Kbit
Total delay is 3000 microseconds
Reliability is 255/255
Load is 1/255
Minimum MTU is 1500
Hop count is 2
Read more...